Flare-On 8 Challenge 8 - beelogin
We are given a huge HTML file with lots of Javascript in it. On first glance, there seems to be a lot of redundant code.
Filtering the Javascript
Upon looking through the Javascript, it seems that removing the miscellaneous functions within the Add function would help to clean up some stuff.
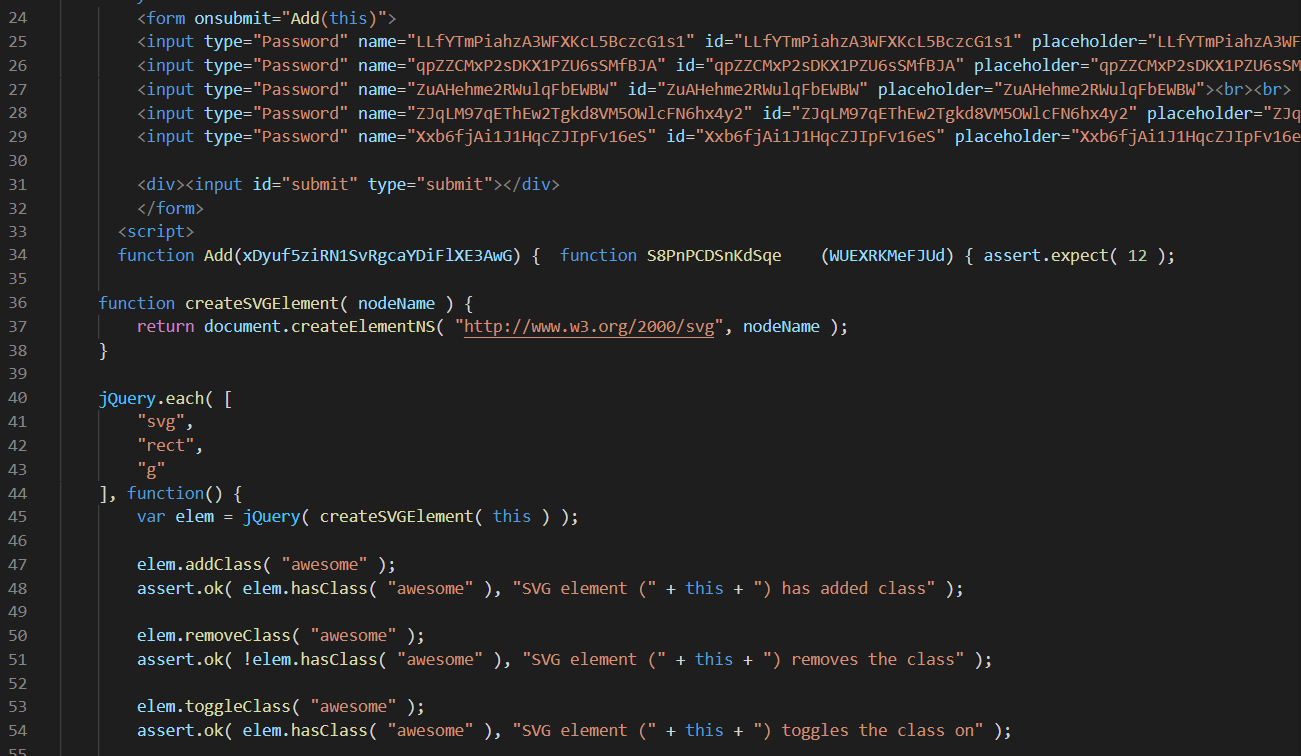
Through discussions with a friend, he told me that we could actually use vim to remove all defined functions within Add through the usage of macros.
To remove all inner functions using vim, perform the following:
- Type
qqqto clear all registers - Type
qqto begin recording the macro - Type
/function<cr>f{da{dd@qas the macro body - Type
qto finish recording - Navigate to the first line of the
Addfunction and execute@q
This will trigger the recursive macro until all inner functions are removed, and the macro dies(?)
We are then present with minimal JS that is the challenge.
The Algorithm
| |
From the cleaned up Javascript, we can see an array being formed from a base64-decoded string, and being transformed with our key.
The array is then used to decrypt the huge base64 decoded blob. The final output is then passed into eval, to be interpreted as Javascript.
Knowing that the final output is Javascript, we can safely determine that the final output would be in the range of printable ascii characters.
Key Bruteforce
From the algorithm, we can conclude the following:
- Key is 64 bytes long
- nth byte of key affects (n//64 + n)th byte of the first array (
EuF8AepyhtkSXEWvNKIKZMaSHm4v) - Xth byte of
EuF8AepyhtkSXEWvNKIKZMaSHm4varray affects (X//221+X)th
As such, we can draw the conclusion that nth byte of the key affects [(n//64+n)//221+(n//64+n)]th byte of the plaintext.
Following this equation, we can write a script that brute-forces the key byte-by-byte.
The algorithm:
- Init a key of length 64, with the value of the current byte candidate
- Run through the array generation and decryption algorithm
- Find all bytes affected by current byte being brute-forced
- If the bytes contain non-ascii characters, determine the key byte to be invalid and move on
After this process, you should be left with only a few candidates (if not only 1) for each byte of the key. The candidates can be further chosen based on the resulting output and if it make sense.
After doing so, a JSFuck script will be decrypted.
Upon decoding the JSFuck, another similar JS script to the original JS will be revealed. Repeat the process and get another JSFuck script. Decode that and get the flag.
key1: ChVCVYzI1dU9cVg1ukBqO2u4UGr9aVCNWHpMUuYDLmDO22cdhXq3oqp8jmKBHUWI
key2: UQ8yjqwAkoVGm7VDdhLoDk0Q75eKKhTfXXke36UFdtKAi0etRZ3DoHPz7NxJPgHl