Flare-On 8 Challenge 5 - FLARE Linux VM
We are given a VM for this challenge, and that is all we have to work with.
Getting the Binary
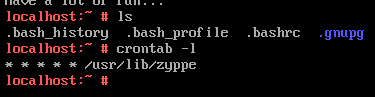
Viewing the cronjobs of the VM reveals a binary in
We can then extract the binary out of the VM via scp.
Binary Analysis
A quick look into main reveals references to the Documents directory.
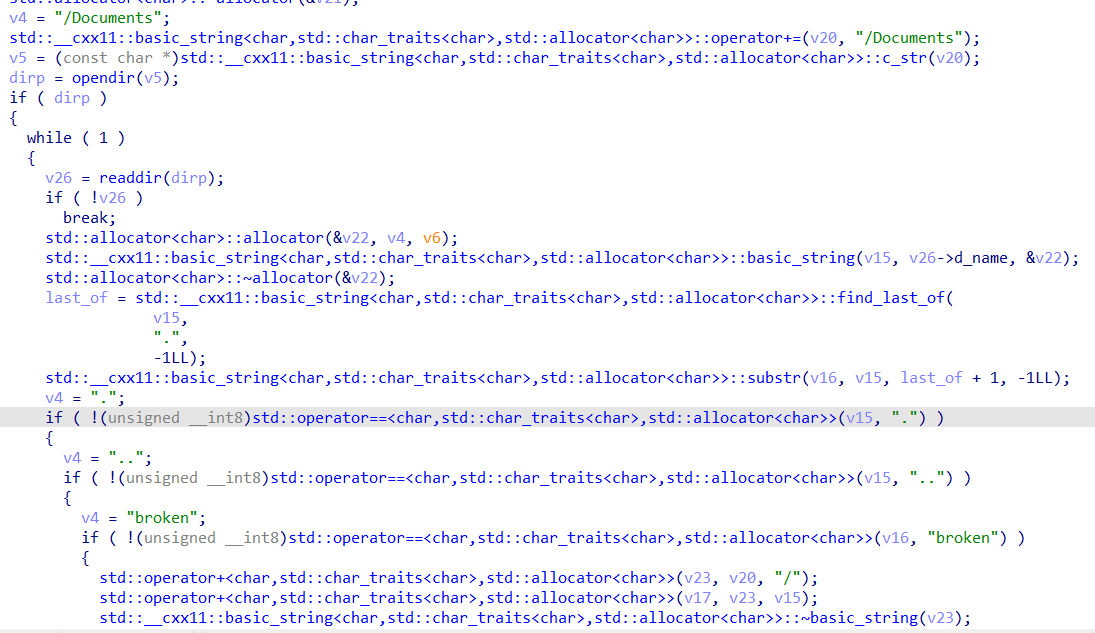
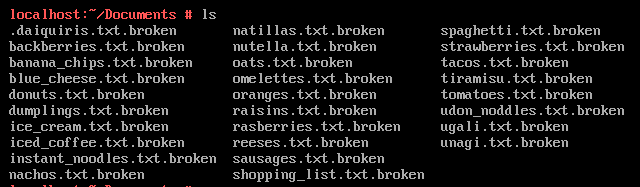
We can find several encrypted files in the Documents directory.
Further down in main of the binary, we can find a function named encrypt
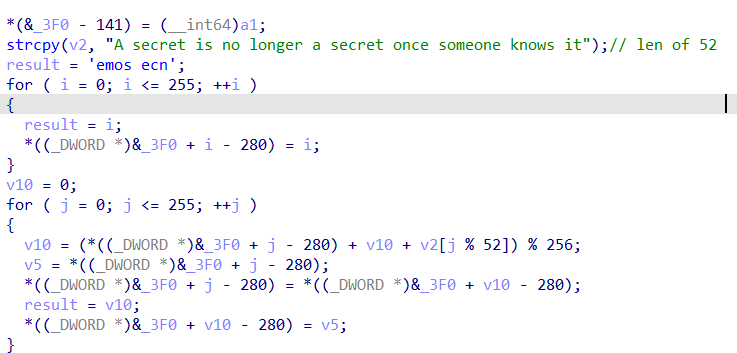
To experienced malware analysts and reverse engineers, they would instantly recognize this function as RC4.
When I was attempting this challenge, I did not realise so.
What I did realise, was that the encryption algorithm was easily reversible to get back the plaintext.
My train of thought:
- Each char of each file is XORed using a lookup table generated at runtime
- Good news is that the lookup table can be reimplemented using the same algorithm at each iteration
- Given that the encryption is just XOR, the binary’s encryption algorithm could pretty much be re-used for decrypton.
Upon decrypting the files, only some files were in plaintext, which revealed clues to the “next step”.
The summarised clues are as such:
A bruteforce script was written as some bytes were unclear due to bad decryption(?) or unknown answers to questions in the hints. Since only 2 bytes were unknown, the bruteforce script runs relatively quickly.
The password found is E4Q5d6f`s4lD5I
Getting the Flag
From the hints gathered, we are pointed towards /usr/bin/dot as another binary to investigate.
Upon executing the binary, it turns out to be a password checker which would decrypt the flag using the input key.
By entering the password we had found, the binary reveals the flag.