Flare-On 8 Challenge 4 - myaquaticlife
We are given a GUI application, with 16 different buttons to click on. It seems that when the buttons are clicked in the correct order, the flag will be displayed.
Extracting MMBD File And Analysis
Upon digging into the strings, we can find references to Multimedia Builder. A quick search on Github reveals a project that helps to extract the original multimedia builder file.
After extracting the mmbd file and opening it Multimedia Builder, we can see a plugin object.
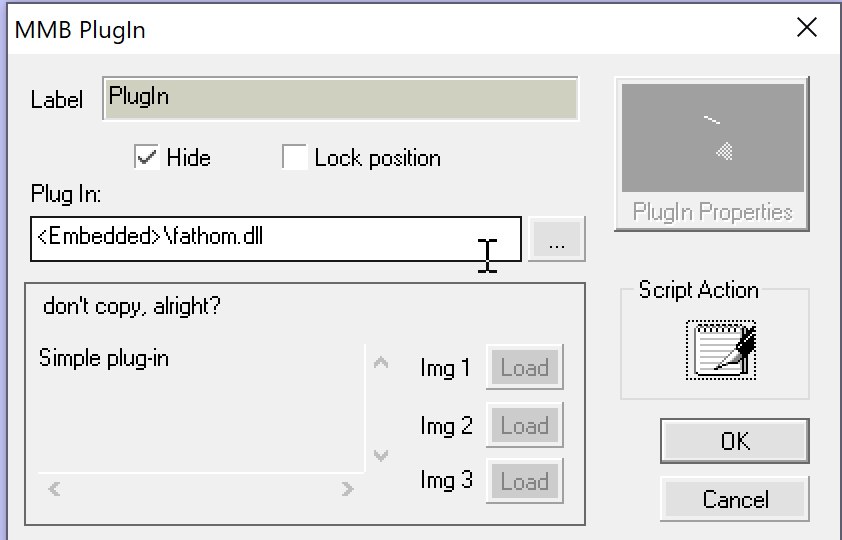
The plugin appears to be a DLL that would be dropped to %APPDATA\Local\Temp\MMBPlayer\. We can extract fathom.dll from there.
Each button also seems to represent a value, passed into the plugin.
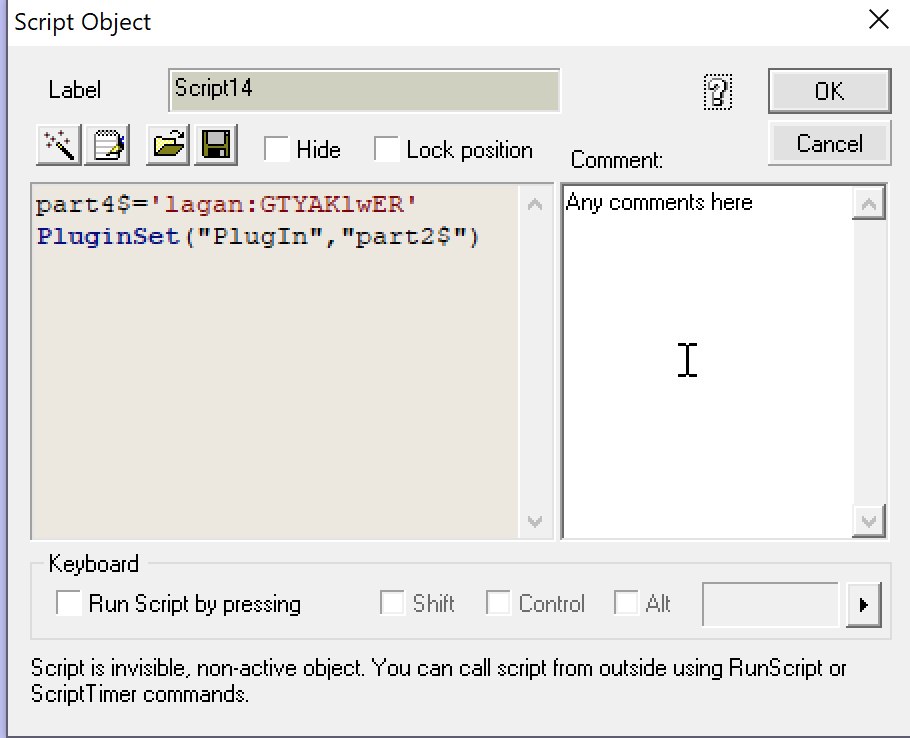
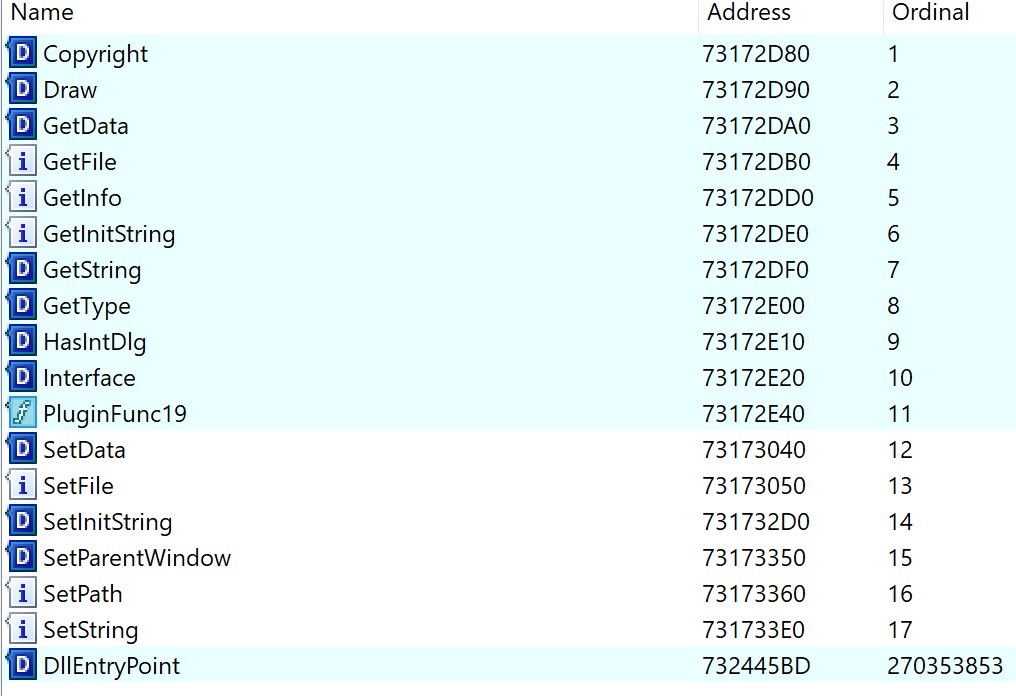
DLL Analysis
Looking into the exports, we can see the PluginFunc19 function.
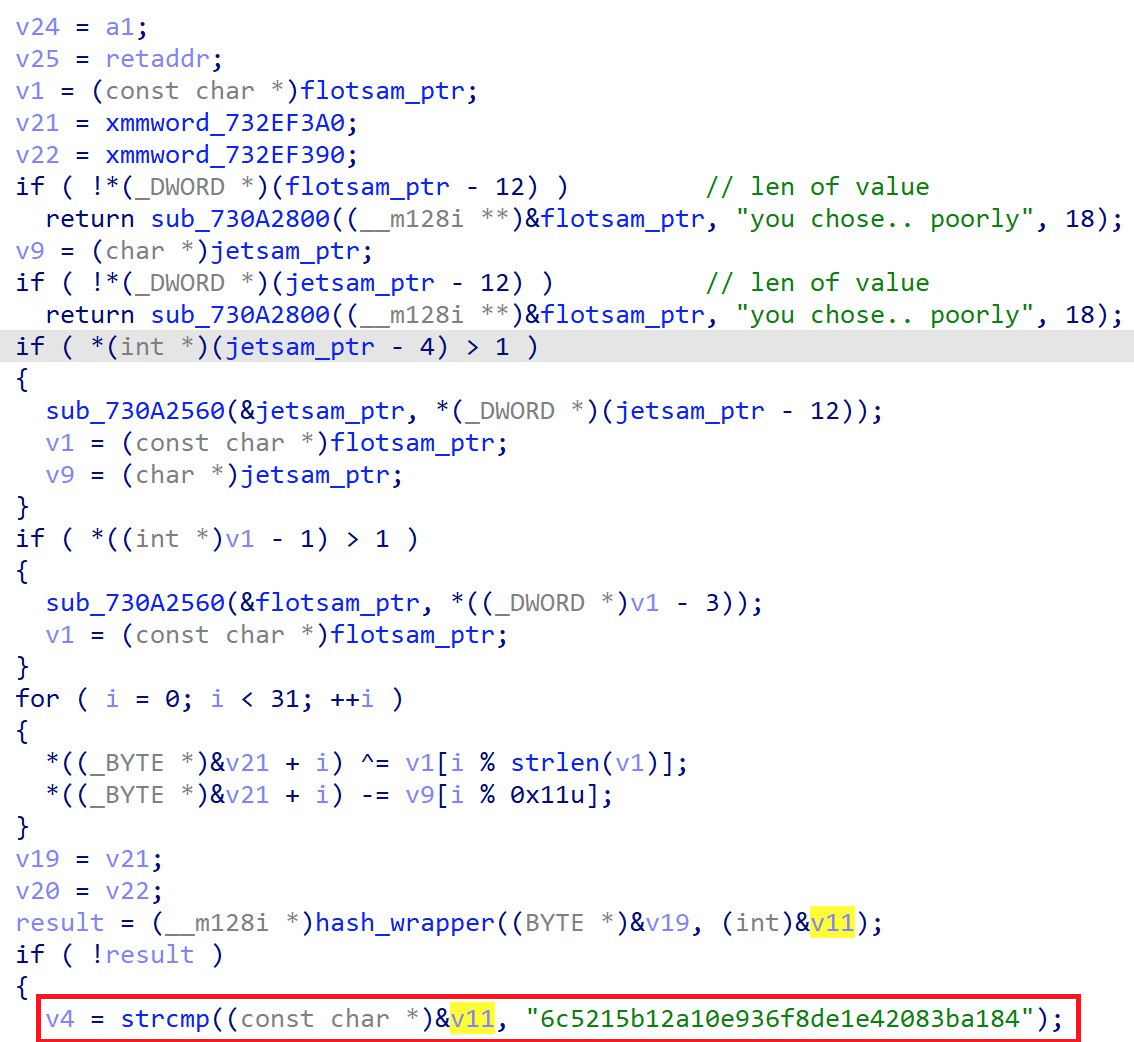
Within the function, we can see that it takes a pointer to the strings referencing jetsam and flotsam and using them to transform a static hex value: 9625A4A9A3969A909FAFE538F9819E16F9CBE4A4878F8FBAD29DA7D1FCA3A800.
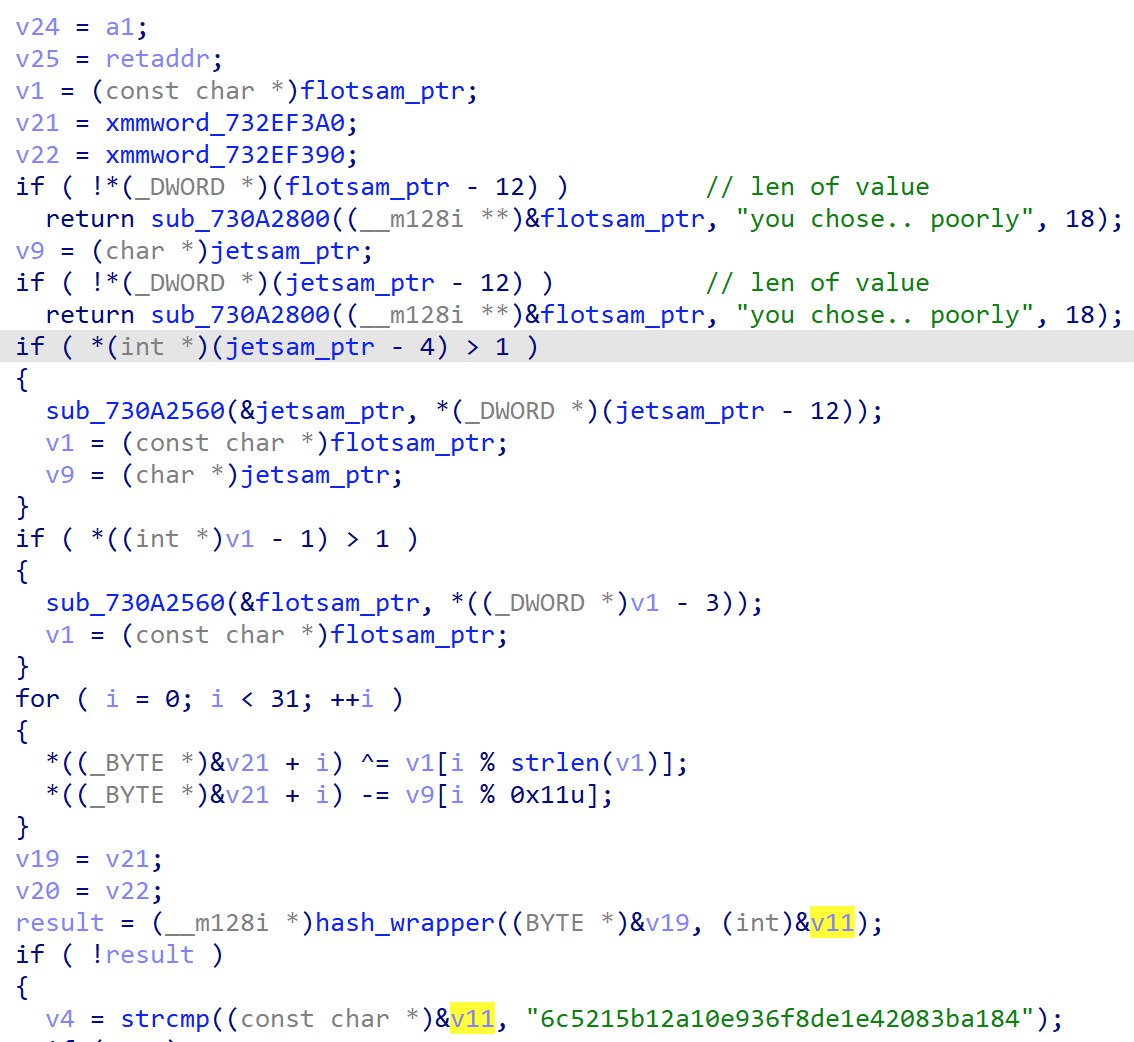
The transformed value then goes through a hashing function.
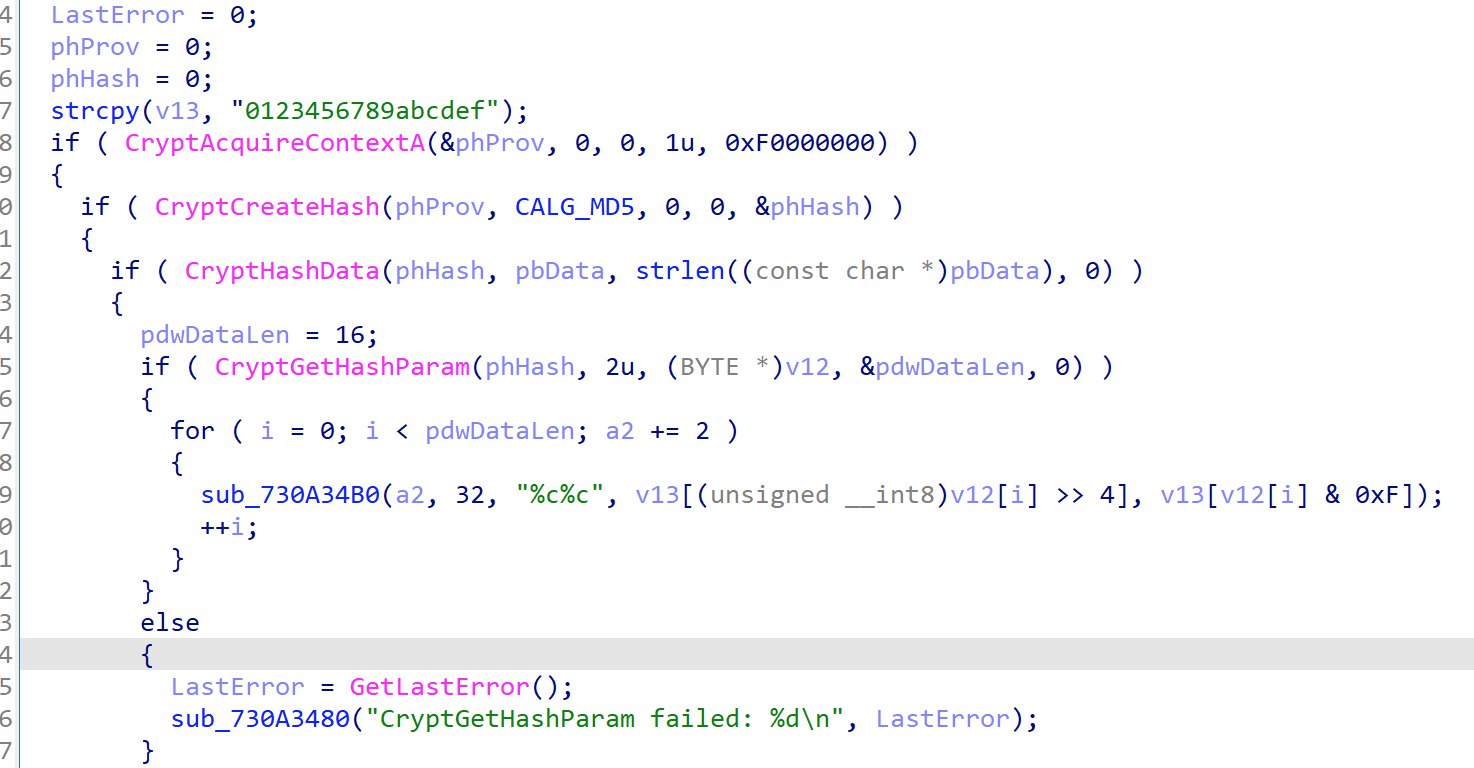
The transformed buffer is hashed using MD5 and placed into a char array, similar to hex_digest in Python’s hashlib
The hash is then compared to 6c5215b12a10e936f8de1e42083ba184 via a strcmp.
Getting The Flag
We can bruteforce valid inputs and check if we get the same hash. That would allow us to find the valid inputs to enter into the program.
The algorithm is as follows:
- Extract the different value relating to
jetsamandflotsam - Reimplement the transformation function
- Build a list of all permutations of values (I used
itertools) - Run all permuations through the transformation and hash it
The script to solve this can be found on my github
jetsam input : [SLdkv,newaui,HwdwAZ]
flotsam input: [PXopvM,DFWEyEW,BGgsuhn]