Flare-On 8 Challenge 2 - known
The challenge provides the a decryptor for the files. Simple RE can be done to deduce the encryption algorithm.
Binary Analysis
Looking into the binary, we can easily find the decryption routine.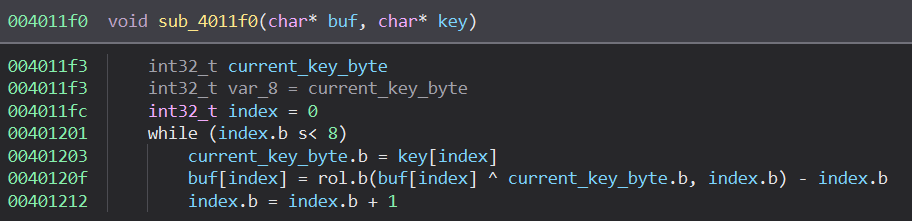
The contents of the file is decrypted by XOR-ing the key with the ciphertext, rotating the bits left by the index, followed by subtracting the value of index.
This decryption routine is done multiple times.
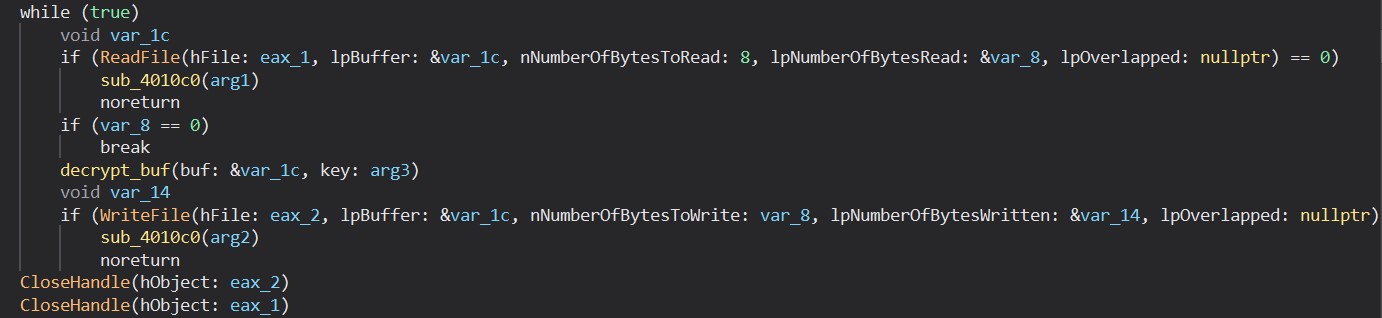
The contents of the files are decrypted in blocks of 8, which suggests that the length of the key is 8.
Key Derivation
Since simple XOR is used, we can easily deduce the key used. Among the encrypted files, there are PNG files.
PNG files have a 8 byte file header of 89504E470D0A1A0A. We can use the known plaintext bytes to derive the key.
Steps:
- Add index to the ciphertext byte
- Rotate the ciphertext byte by index
- XOR with known plaintext bytes
This process results in the key: No1Trust.
Solving
With the key, we can simply run the decryptor to automatically decrypt all files in the directory and get the flag.