DFIR Playbook
IR Lifecycle
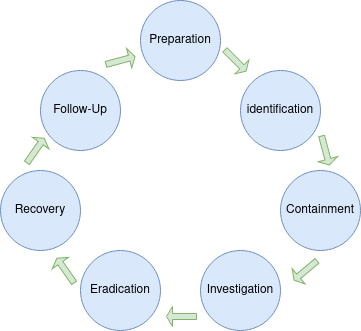
Each phase of the lifecycle must be complete before the next phase can begin.
Incomplete identification can lead to incomplete containment, and incomplete investigation can cause backdoors to be left in network even after eradication.
Following this lifecycle helps to provide a structure of how to conduct Incident Response.
Host Artifacts
Powershell Logs
Logging is not enabled by default
Enable logging at Administrative Templates → Windows Components → Windows PowerShell
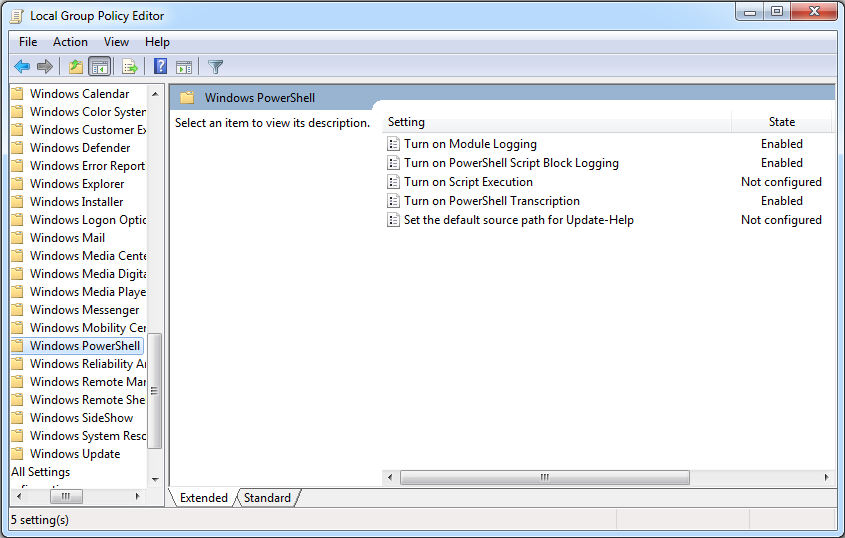
Alternatively, set registry keys:
- Records all Powershell Sessions' input and output, similar to `bash_history`
HKLM:\SOFTWARE\Policies\Microsoft\Windows\PowerShell\Transcription
→ EnableTranscripting = 1
→ EnableInvocationHeader = 1
→ OutputDirectory = "" (empty for default path)
- Logs code as they are executed by the PowerShell engine
HKLM:\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
→ EnableScriptBlockLogging = 1
→ EnableScriptBlockInvocationLogging = 1
Logs at following locations:
C:\Users\**\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log -> .NET runtime libraries loaded during last sessions
C:\Users\**\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt -> history of commands (records only interactive PowerShell sessions)
C:\Windows\System32\winevt\Logs\Micorsoft-Windows-Powershell%4Operational.evtx -> errors & interrupts
Windows Event Logs
| Event ID | Description | Red Flags |
|---|---|---|
| 4624 | A user successfully logged on to a computer | Logon Type != 5 (Service Startup) |
| 4625 | Logon failure. A logon attempt was made with an unknown user name or a known user name with a bad password. | |
| 4634 | The logoff process was completed for a user. | |
| 4647 | A user initiated the logoff process. | |
| 4648 | A user successfully logged on to a computer using explicit credentials while already logged on as a different user. | Event itself might suggest pivoting |
| 4779 | A user disconnected a terminal server session without logging off. | |
| 5140 | A network share object was accessed. (Windows logs this event the first time you access a given network share during a given logon session) | Might indicate information gathering |
| 5142 | A network share object was added. | |
| 5143 | A network share object was modified. | |
| 5144 | A network share object was deleted. | |
| 5145 | A network share object was checked to see whether clients can be granted desired access. | Might indicate information gathering |
Other Host Artifacts
Prefetch
Can be used a source of evidence to indicate executable files that previously ran on the system.
Parsing the contents of these files can yield:
- Date and time of first execution (corresponding to the prefetch file creation date)
- Last run time (stored within the prefetch file)
- No. of times executed (stored within the prefetch file)
- List of files accessed during the first ten seconds of execution (stored within the prefetch file)
- Full path to executable file (derived from accessed file list)
Prefetch files can be found @ C:\Windows\Prefetch\
Application Compatibility Cache aka ShimCache
ShimCache can be used by investigators to determine the application and programs executed on a compromised system.
The cache contains the following important information:
- File Path
- Standard_Information Last Modified Time
- ShimCache Last Updated Time
- Process Execution Flag
Not all entries in the ShimCache are resultant of program execution. This is where the process execution flag becomes crucial.
The ShimCache works on a rolling basis, new entries would eventually overwrite old entries. As such, try to secure this artifact as soon as possible.
ShimCacheParser.py by Mandiant can be used to analyse the ShimCache
Amcache
The Amcache is a registry hive file which stores information related to program execution
Only the File Subkey of the Root key is of importance.
The subkeys under the File key are grouped according to the volume GUID. Under each of those volume GUIDs are File Reference keys, each representing a different file.
On NTFS systems, the entries follow the format: <NTFS File id><sequence number>. On FAT systems, the entry represents the offset from the start of the volume where the file directory entry exists.
The following illustration of the Value Names(subkey of each entry) was taken from swiftforensics’s site: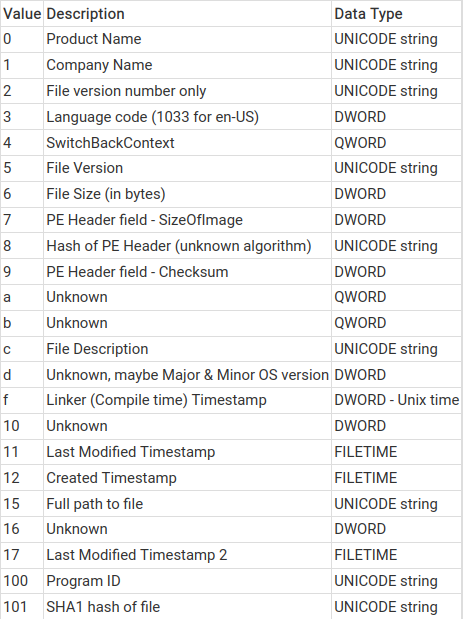
The hive file can be found @ %SystemRoot%\AppCompat\Programs\Amcache.hve
Windows Activity Timeline
The Windows Activity Timeline contains the following information:
- Application name
- Time of launch
- Usage duration
- Files accessed using application
- Copy & paste history
- URLs visited by application
According to a blog post by Cellebrite, the data is generally kept for 30 days.
The applications executed by the user can be found in the App Id column of the Activity table.
The information is stored in a database @ C:\Users\<user>\AppData\ConnectedDevicesPlatform\<folder>\ActivitiesCache.db
Master File Table (MFT)
$MFT can give insights into files that were dropped and used by adversaries, that were later removed from the system.
The MFT contains information of when files were:
- Accessed
- Modified
- Changed
- Created
The MFT can be parsed using Mft2Csv
The csv file can then be used to look for artifacts and evidence during the suspected timeframe.
Memory Forensics
Acquiring memory snapshot would likely result in addition and changes to host artifacts. Recommended to do as last resort.
Pros:
- Everything that happens on a computer happens in memory
- Every command entered
- Every file opened
- Crucial if no other logging is in place
- Can be used to propel investigation during host forensics
Cons:
- Heavy
- Takes up significant time
- Addition and modification of artifacts on host